So your or yours client website got hacked? It’s all too common to hear of Joomla 1.5 (or Joomla 1.6) sites getting hacked over and over, administrators addressing the symptoms but, without tackling the root cause, wondering why they’re so unlucky. They just use temporary solutions, keep applying band-aids without cleaning the wound and bad infections come back sooner or later.
Because manually diagnosis can take time, that can mean downtime. That’s why I suggest to use standalone security scanners like Joomla! Anti-Malware Scan Script (github.com/btoplak/Joomla-Anti-Malware-Scan-Script). This a self-service script that will be continually programmed to assist all Joomla! owners to check their Joomla! installation for various trojans and other web-malware. The script currently uses regex patterns to identify the most common fingerprints, traces and indices that some files have/could’ve be compromised. This script still doesn’t do any cleanup on its own, it’s only informative about some suspicious code in your Joomla! installation. This script is far from being 100% accurate. It has just a few patterns at this moment, and the false-positives are very well to be expected. So you may only use it wisely and with caution.
JAMSS Usage Instructions
The usage is pretty simple and straightforward:
- Upload two files uzipped before from: btoplak-Joomla-Anti-Malware-Scan-Script.zip (jamss-X.Y.Z.php and jamssPatterns.php) to the webroot of your hosting account. But before that make sure that your sever using at least PHP 5.
- Open the scanner file in your browser using URL like this http://www.your-joomla-site.com/jamss-X.Y.Z.php
- The script will run for several seconds, maybe even minutes, depending on number of your files and load on your webserver.
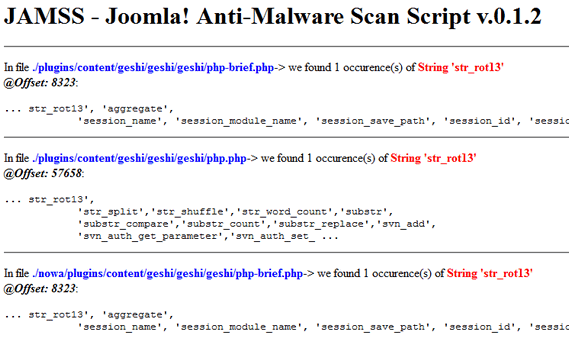
Example report page from Joomla 2.5 – of course, you need to verify all messages about vulnerabilities.
Hacked or not hacked?
If you’ve clearly been hacked or are trying to wrap your head around an uncertain issue, to play it safe, bring the site safely down into offline mode. After that visit:
- http://sitecheck.sucuri.net/scanner/
- and http://safeweb.norton.com/ – enter the URL of our website and look forward. After a while, you find out if your website is on the black list.
Than try to find all unauthorized modifications in Joomla files. After (or better before!) clearing the site from suspect code, change all passwords, whether for FTP, MySQL, SMTP authentication (Site -> Configuration -> Server -> Mail) and to the administration panel!
By they way, you can use also OWASP Joomla! Security Scanner (check the usage manual), but this script has last update few month ago. On the http://hackertarget.com/joomla-security-scan/ you can use a scanner that uses this script but there offered free option “Passive” does not give you much information on the safety side, while the “Active” is paid (commercial).
However, remember that prevention is better than cure, that’s we have decided to partner with SiteGround WebHosting. They are a pioneer in making shared hosting more secure for open source applications like Joomla and WordPress. They have invented a system for account isolation that prevent hackers from accessing multiple installations through a single vulnerable account.